If you were redirected here after entering your credentials, please read on to learn why the email you received was phishing. Don’t worry! This was a simulated phishing attempt so your credentials are safe. However, if the situation were real, the information you entered would now be in the hands of a cybercriminal.
The email you received was sent by Technology Services to simulate a real phishing email as part of National Cyber Security Awareness Month. Visit pugetsound.edu/NCSAM2020 for more information. The goal of simulated phishing is to provide an interactive way for campus members to learn how to quickly recognize and handle phishing emails.
What was suspicious about this email?
- Were you expecting it? If you were not expecting a shared document, use caution before clicking links or opening attachments.
- Did it seem overly vague? There is no name associated with who shared the document which should be suspicious. Something generic like “committeechair” or “departmentchair” are frequently used in phishing attacks. Further, the document title seems vague enough to seem relevant to anyone.
- Was the email address from Google? If you look closely at the sending email address, it was sent from the domain “gooogel.net” instead of “google.com.”
- Did you notice an odd character? In the first line of the message, the email address listed is “pugetsøund.xyz”. Attackers frequently use homoglyphs (i.e. characters that appear almost identical or similar) to impersonate organizations. Look out for deliberately mispelled company names or homoglyphs in email addresses and URLs.
- Did the link go to Google Drive? If you hover over the link to open the document, you’ll notice that the link leads to pugetsound.xyz. That is neither the university’s website nor the website for Google Drive which should be a red flag.
- Did information seem mismatched? The email states there is a new document. However, the logo is for Google Sheets, not Google Docs. It also again lists Google Sheets above the mailing address.
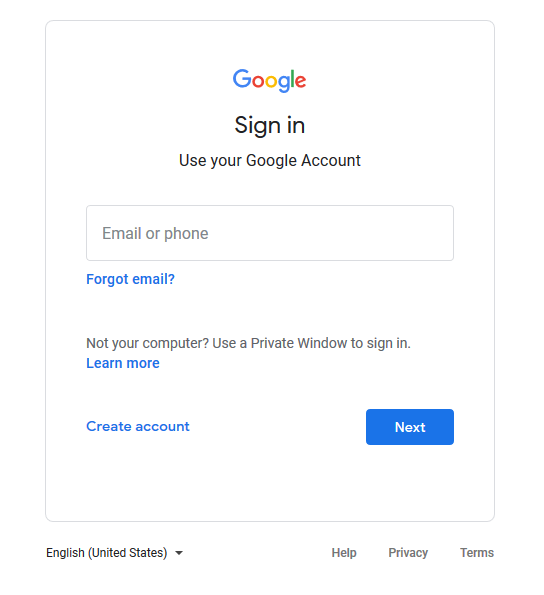
Didn’t the link take me to Google?
Nope! Just because a website has the logo of the company you are expecting does not mean it is legitimate. Be especially careful on sites where you enter your username and password. If you enter your username/password on a website from a phishing email, your account and password are likely compromised. Always double check the URL. In this case, the URL was pugetsound.xyz whereas it should have been accounts.google.com.
Fake Google Login Page

Real Google Login Page
How do I spot other document sharing phishing messages?
Know the deal real! For legitimate shared Google documents, expect the message to be sent with a display name like this: “Jane Logger (via Google Docs).” The sending email address should be: “drive-shares-noreply@google.com.”
If a linked document is password protected, think twice. Many phishing emails use legitimate cloud sharing services such as Google Drive or Microsoft OneDrive. Normally, a file is scanned for viruses before it is uploaded to a cloud service. However, if the file is password protected, the automatic malware scan cannot occur. If you receive a link to a cloud storage site and the email includes a password to unlock the file, use caution. You might be downloading malware onto your computer by clicking the link and unlocking the file.
Original Simulated Phishing Message
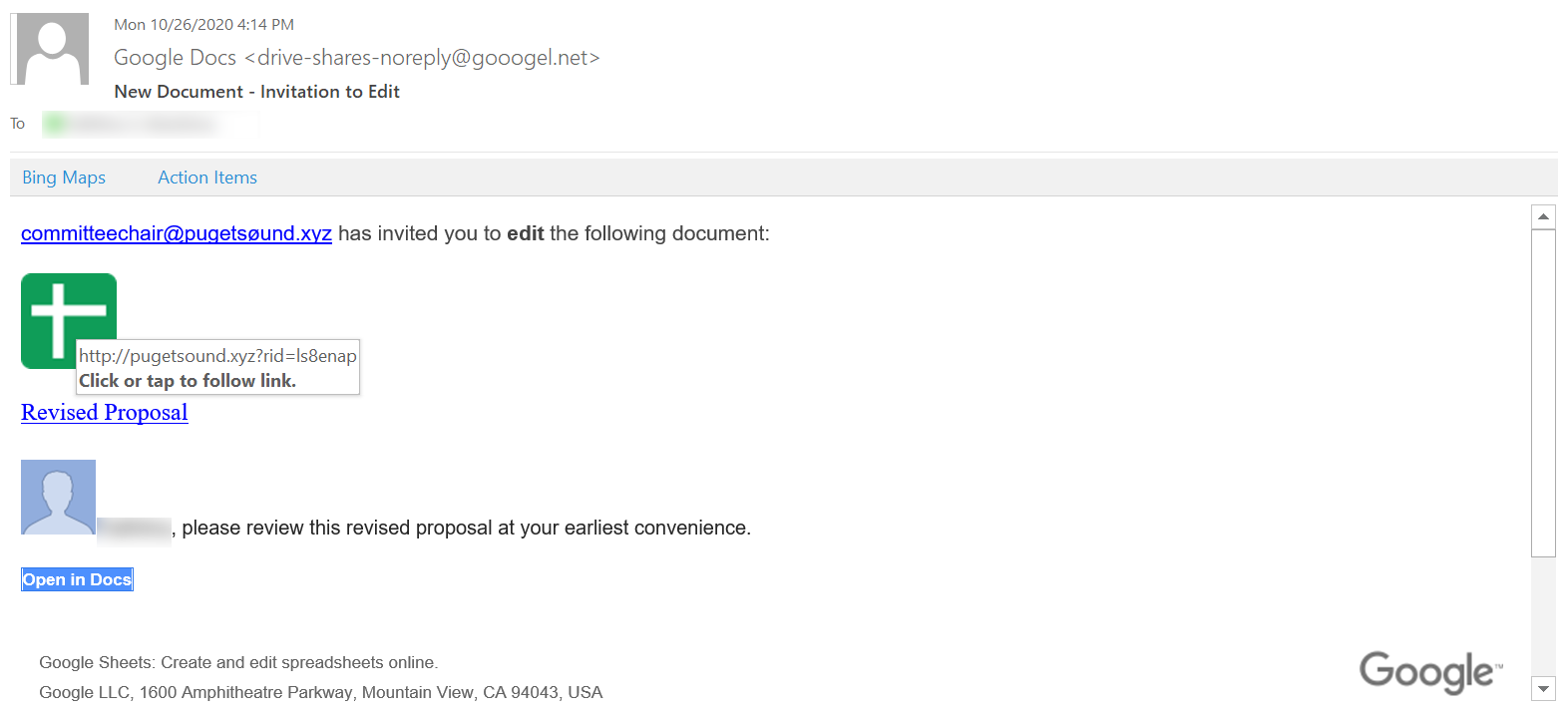
Text of Simulated Phishing Message
committeechair @ pugetsøund.xyz has invited you to edit the following document:
Revised Proposal
[First Name], please review this revised proposal at your earliest convenience.
Open in Docs
Google Sheets: Create and edit spreadsheets online.
Google LLC, 1600 Amphitheatre Parkway, Mountain View, CA 94043, USA